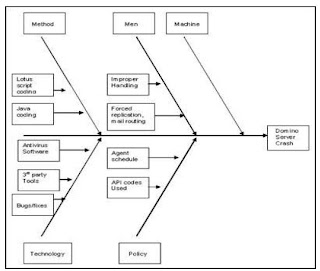
Cause-effect graphing attempts to provide a concise representation of logical combinations and corresponding actions. A Cause-and-Effect Diagram is a tool that helps identify, sort, and display possible causes of a specific problem or quality characteristic . It graphically illustrates the relationship between a given outcome and all the factors that influence the outcome.Causes (input conditions) and effects (actions) are listed for a module and an identifier is assigned to each.
A cause-effect graph developed.
Graph converted to a decision table.
Decision table rules are converted to test cases.
The C&E diagram is also known as the Fishbone/Ishikawa diagram because it was drawn to
resemble the skeleton of a fish, with the main causal categories drawn as "bones" attached to the spine of the fish.
 Advantages
AdvantagesHelps determine root causes
Encourages group participation
Indicates possible causes of variation
Increases process knowledge
Identifies areas for collecting data
Comparison Testing
In some applications, the reliability is critical.
Redundant hardware and software may be used.
For redundant s/w, use separate teams to develop independent versions of the software.
Test each version with same test data to ensure all provide identical output.
Run all versions in parallel with a real-time comparison of results.
Even if will on run one version in final system, for some critical applications can develop
independent versions and use comparison testing or back-to-back testing.
When outputs of versions differ, each is investigated to determine if there is a defect.
Method does not catch errors in the specification.
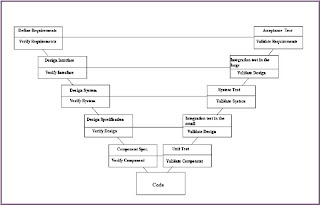
TESTING PROCESS PART THREE
WHAT TEST PLAN SHALL HAVE ?
SOFTWARE RELIABILITY
TEST DESIGN
DEFECT CLASSIFICATION
DEFECT TRACKING
TEST METRICS
TEST REPORTS
CHANGE REQUEST MANAGEMENT
UNIT TEST SPECIFICATIONS
UNIT TEST SPECIFICATIONS PART TWO
FUNCTIONAL FLOW MATRIX PART ONE
FUNCTIONAL FLOW MATRIX PART TWO
PROGRAM INSPECTION AND REVIEWS
CODE INSPECTION IN SOFTWARE TESTING