-
analysis— which focuses on understanding the problem and defining the requirements for the software portions of a system
-
design— which focuses on solving the problem in software
-
implementation— which focuses on translating the design into executable code
-
testing— which focuses on ensuring that inputs produce the desired results as specified by the requirements
Under an incremental development process, a system is developed as a sequence of increments. An increment is a deliverable, including models, documentation, and code, which provides some of the functionality required for the system.
The products developed in one increment feed into the development of the next increment. Successive increments add (and sometimes change) system functionality. The final increment delivers a deployable system that meets all requirements. Increments can be developed in sequence or one or more can be developed concurrently.
To build each increment, developers analyze, design, code, and test as needed. They typically have to perform these activities repeatedly in building an increment because they find errors in previous work. As development progresses, they gain new insights into the problem and the solution. We prefer to acknowledge this iterative aspect of incremental development and make it part of the process.In planning each increment, we include explicit steps for repeating various activities. Among these are steps for systematically reviewing current models, identifying errors based on experiences in later tasks, and modifying the models (or code) that have already been produced—not just those that will be produced in the future.
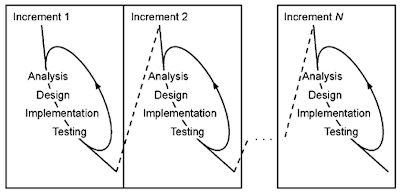
Object-oriented development is particularly well suited to evolutionary development because object-oriented analysis, design, and implementation entail the successive refinement of a single model. This is the case both within an increment and among increments.
In object-oriented analysis, we understand a problem by modeling it in terms of objects and classes of objects, their relationships and responsibilities. In object-oriented design, we solve the problem by manipulating those same objects and relationships identified in analysis and introducing solution-specific classes, objects, relationships, and responsibilities.
Implementation is straightforward from a well-specified set of design products. Thus, the entire development process involves a refinement of a model. Design products are primarily an extension of analysis products and implementation products are coded expressions of design products. The products of one increment are extended and refined in the next increment.
The incremental development of products requires the incremental testing of those products. Products can change from increment to increment in both planned and unplanned ways. Test suites must change in concert. Regression tests must be run between increments and within iterations to ensure that changes do not adversely affect correctly working code.
A process in which work on one increment overlaps work on another adds to the complexity of development and testing. Coordination is required to sequence the development of interacting increments so that objects that are associated with, but assigned to different increments, can be tested in a timely fashion.
Software testing other interesting topics:
Programming c language introductionCLASSES AND OBJECTS IN JAVA
JAVA PROGRAMMING ENVIRONMENT
JAVA EXECUTION
JAVA CONSTRUCTORS
FIELD DECLARATIONS IN CLASS OF JAVA
EXCEPTIONS IN JAVA
EXCEPTIONS IN JAVA PART TWO
VARIABLE PARAMETERS IN JAVA
COMMENTS TYPES AND VARIABLES
JAVA JDBC AND ODBC
INTERFACE IN JAVA
OPERATORS IN JAVA